
Today we’re going to discuss the Clean Desk and Clean Screen policy. As a company who’ve recently made the journey towards ISO 27001 certification, we’ve asked one of our veteran colleagues to relate his tale as it was: Hi – It’s “the other Alex”. This time I’m going to write about something a little out of my league that had a direct impact on my workflow. It is mostly, a story about habits and transformation that happened during an important transition within our company. Just last year, our company passed its ISO 27001 certification and here, is where the “Clean Desk Policy” kicked in. My kryptonite, or my Achilles’ heel. Why’s that? Well, let’s move forward and explore my meandering experience of changing habits.
The “before” perspective
You see, back then I was still deep into prototyping, copywriting, wireframing and in some instances, UX flows. Naturally, this required consulting various pieces of information at once. It meant hundreds of tabs torturing my PC, dozen sticky notes on my monitor, piles of research papers, outlines, blueprints and about 2 or 3 yellow pads full of pencil sketches I used to draft during some of my extended breaks. Anyone who’s in the “creative” line of things knows: If there’s no mess on your content delivery officer’s desk – they’re probably doing it wrong – right?

Wrong! Looking back, I might just have to admit – the above were excuses. After all, even to date, I can cope with a generic sketch pad for carrying my daily tasks, without risking any critical data exposure.
Not to say that I was completely reckless regarding security. I’d rarely have confidential stuff on my desk. However, after getting a bit more into Data Protection and other provisioning lists of EBSs’ “Clean Desk Policy”, I must admit: what seemed innocent at first, became slightly qualified as private. I’m talking about the occasional name and phone number on a sticky note, some annual leave documents or an older report that someone really needed printed.
It wasn’t a big deal since I had those on my desk, for less than 15 minutes before filing them in the right cabinet or recording that contact data in the CRM. Once I was even qualified as the “fire hazard person of interest”, because of my lack of trust in our shredder. Long story short, I used our backyard barbeque to incinerate whatever was digitized or no longer useful – with proper supervision. All of this stopped when we moved to the new office where I had neither a backyard nor a barbeque. And adding insult to injury: I was no longer supervised.

I guess, for the time being, a shredder should do – otherwise we’ll have to implement the IBM’s security classification: “For Employees Only to Read and Eat”.
The long-awaited Definition
Since most of our audience is (and I quote): “Classy Tech and Business Nerds” – I’ve made an educated assumption: y’all know what a “Clean Desk Policy” is – Right?
Just to fill in the gaps for those who don’t, I’ll make it crystal clear: this does not involve cleaning your desk twice a week with lemon pledge. That’s highly recommended (given the current COVID19 state) but has nothing to do with what I’m about to define here. Still, wash your hands as often as you can.

Now, the actually “commonly adopted” definition, states the following:
A Clear Desk and Clear Screen Policy (CDCSP) is a procedure enforced by the Management, that is designed to protect information stored on physical and electronic media, to minimize the risk of unauthorized access.
For those who are more or less familiar with the Cyber Security terms, such policies are considered “Physical Access Security Measures”. If you’ve been around here for a while, you’re quite familiar with our quote: “humans make mistakes which in turn leads to vulnerabilities” – and here, CDCSPs come to the rescue (when properly implemented).
In human terms, a Clean Desk and Clean Screen Policy is simply a protocol that defines or specifies requirements for how everyone within an organization, should handle company information and materials within the office. It should include requirements for computers, mobile devices, access cards, and printed materials, as well as for how workspaces should be maintained.

Furthermore, if you’re a reputable Bespoke Software Delivery Provider, such regulations are an absolute must – especially since these are paramount to ensure security compliance with regulations such as ISO 27001 and the Data Protection Act.
The Transition from “religion” to Clean Desk and Clean Screen Policy
As mentioned, I got to understand things from a different perspective, once we’ve decided to get the ISO/IEC 27001 certification. The moment we went that path, our HR, together with the Chief Information Security Officer, gathered us for yet another “Monthly Training”. Initially, the requirements were nothing new. We did have most of the procedures in place already, and some were a complete default since we’re protecting stakeholder confidential information since 2011. We all adhered to NDAs and other nondisclosure mechanics and were somewhat ready to be certified from day 1.
Things we had in place before the Clean Desk and Clean Screen Policy
Just to give you an idea, here’s a short-ish list of what we’ve been doing prior to our certification and are practicing it this date:
- All of our PC’s and terminals are password-protected with the requirement of changing those every *undisclosed* days;
- None of our terminals are left unattended while logged on (let’s just say we have a funny way to train the Winkey + L / Ctrl + Alt + L / Control + Command + Q habit);
- Each and every machine (except datacenter equipment – duh…) are shut down at the end of the workday;
- All of our terminals lock after 3 minutes of inactivity (no screen savers allowed) with a password prompt + MFA to unlock the station;

- Everyone who is cleared to use External Media Storage (any kind of EMS) or uses printed confidential information to carry out its tasks; has a desk locker, where everything is stored when leaving the office or the workspace – any confidential documents too;
- None of our printers are set to clear their cache once the print job is done and every piece of paper is cleared as it’s printed;
- Whatever qualifies as personal belongings are kept in drawers;
- Computer screens are always angled away from the view of unauthorized persons;
- All critical facilities (like network equipment shelves, our Data Center) are locked when not used and access is restricted to authorized personnel only; and
- Of course, all access keys, cards and codes are always stored securely, by their owner.
The new-ish perspective – The Change began
Things became a bit more specific when we’ve been presented the CDCS Policy. For one, I knew the consequences were a tad harsher as compared to the occasional “slap on the wrist” you’d get when something wasn’t exactly following the commandments. When I say “exactly” – I refer to the generic “Eric Called. Follow-up!” note or the “This would attract rats on your desk – maybe put those papers away?” – 99% of the times I obeyed – I thank the universe no one could peek into my locked drawers.

I never saw someone outright sinning against our 10 commandments – those who “allegedly” did – went simply 404. I should probably take a closer look at our CISO and check that backyard for bones… Appealing to the presumption of innocence and leaving dark jokes aside, those who failed to follow the rules were simply not EBS material. They were not given access to confidential info, getting stuck at the most basic authorization level.
When you’re not doing hands-on stuff and prove to be resistant to the way a team works, you weed out eventually. And I could only imagine the horrors our CISO had to go through, without having that policy in place. Considering the Armageddon of cyber threats, its’ experience was anything but a smooth ride.

Pacing in with the right foot, we’ve migrated from generic commandments to an official internal policy. And that’s how my desk clutter had to go. This wasn’t the problem though. Once certain scenarios and the right training have been delivered, I began looking at my tiny sticker notes, those research papers and sketches a tad differently. Suddenly, information I considered as generic, became a “Level 2 Information (Internal Use Only)”. That served as a slight epiphany for me. I kind of knew that my former habit was wrong – but damn… It felt so right! Then again – I thought I still had my virtual desk – and here, the policy kicked in with something else…
”Something else” brought by the Clean Desk and Clean Screen Policy
Following-up on the old amendments, the policy came with some new additions. Per instance, the rule list thickened, and is as follows:
- We were no longer allowed to have files on our desktops – only shortcuts;
- Our displays were secured, in such a way, that any information displayed on our monitors would not be available to unauthorized individuals, preventing them to observe the display output.
- Laptops had to be either locked with a locking cable or secured in a drawer or cabinet whenever our desk was unattended or at the end of the workday;
The “After Effect” of Clean Desk and Clean Screen Policy
I must admit, at EBS we’ve been quite keen about physical security before, so, the after wasn’t as different as the before. All we had to do was to transition from a “religion” of physical security, to a ISP/IEC 27001 backed policy, enforcing our physical security standards. However, when speaking about myself, there were some before/after perspectives.
First, I’ve started using less and less paper. My fast sketches became somewhat laconic, and I no longer needed 3 yellow pads for that. I leave most of my research “in the cloud” and thanks to an additional monitor – it no longer lives on my desk.
Second – I became a bit more conscious about using removable media. I wasn’t keen about using it before; however, since the policy kicked in, I feel safer, since every single removable device I get, gets encrypted with the assistance of our IS team members. Apparently, I was doing it right before (thanks to our “religion”) – but still, it is a tad reassuring to know a guy who’s more qualified than me, validated the process.
Third – I feel safer when having to use my own devices. Prior to our certification those were restricted all together, but since we’ve made secure information processing official, we got another thing: Unified Endpoint Management. This is an internal system that allows me to adhere to security policies (and the Clear Desk and Clear Screen Policy), even when working from home.
All in all, this entire transition started from a Clean Desk and Clear Screen Policy, but it ended as a culture shift, that made my job easier and less cluttered.
And no – I do not miss it anymore. Just to make this clear, here’s a before photo of my desktop (before):
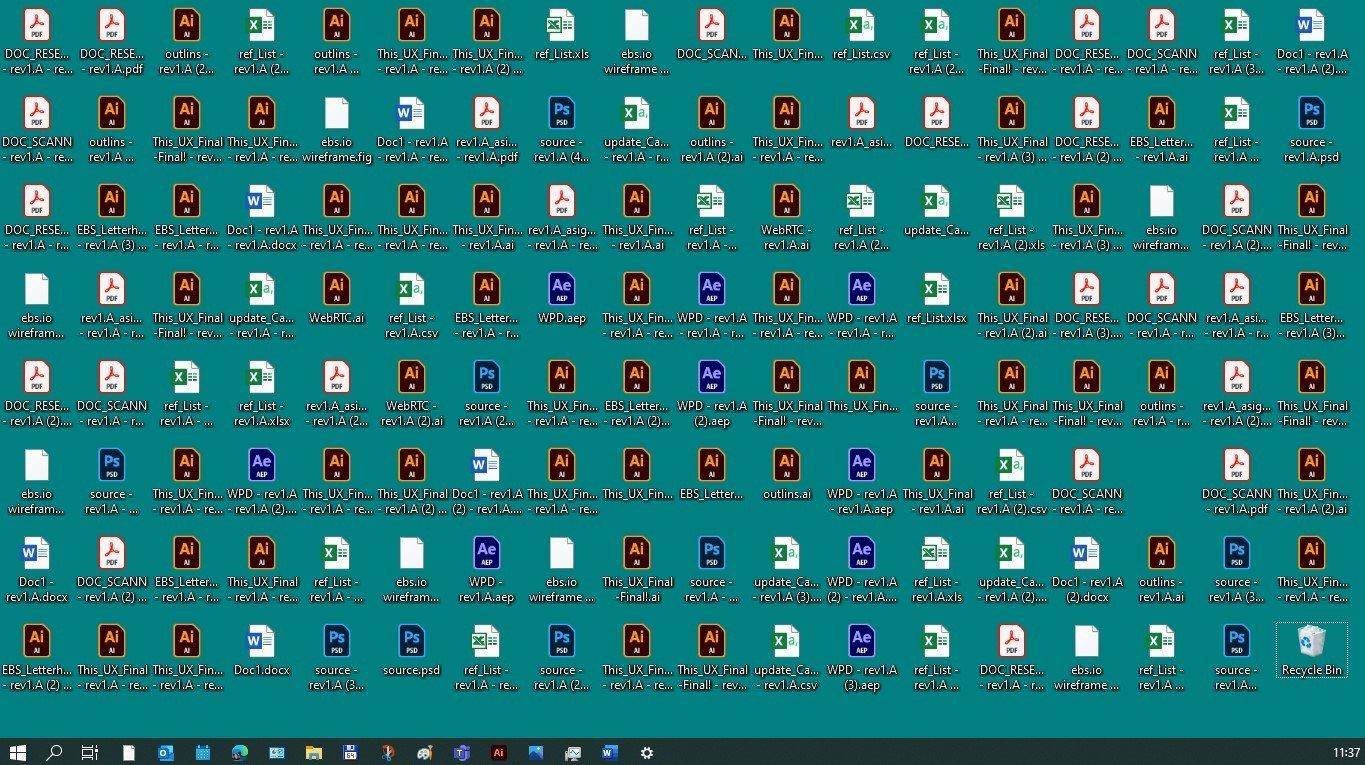
And here is, the after:
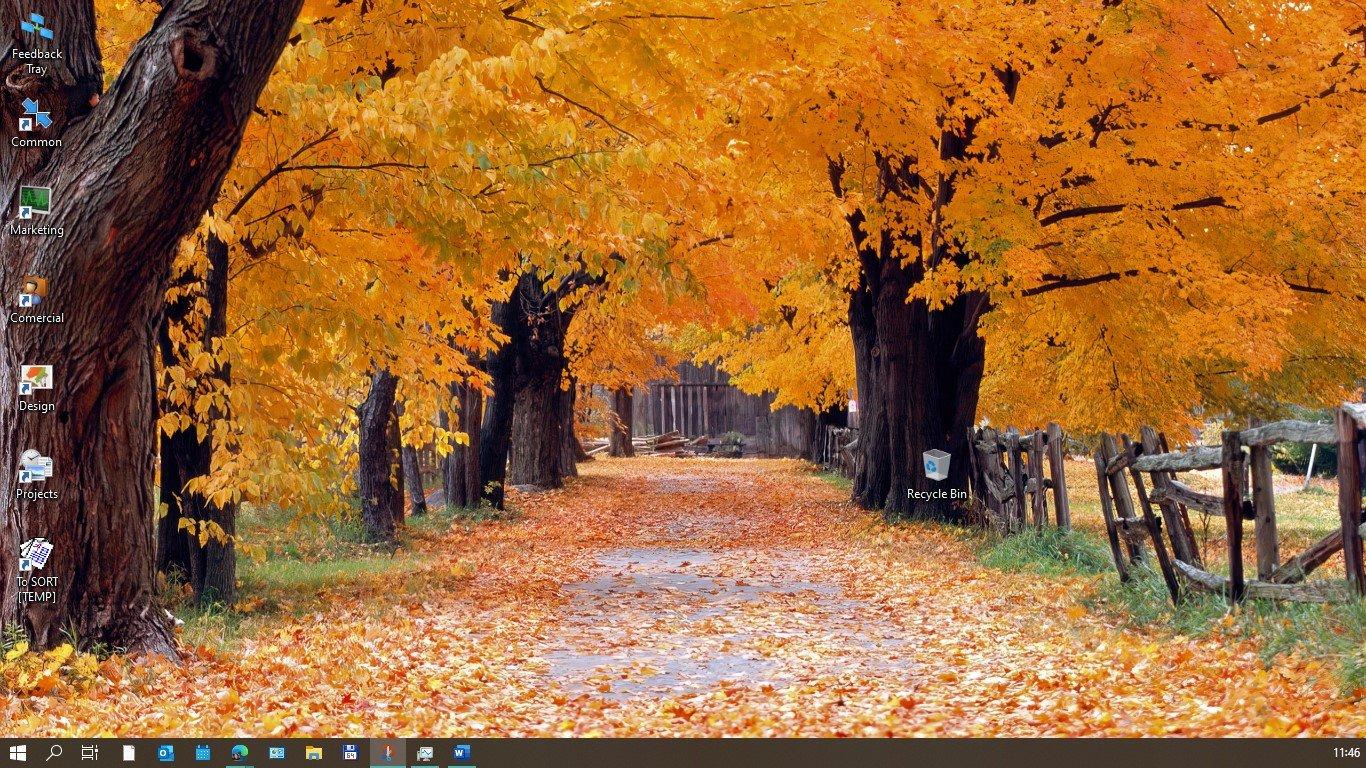
Ye, I got a lot of pats on my shoulder for this, however – that is no the point.
The point + endnotes
What I was trying to say the entire time, is that a Clean Desk and Clean Screen Policy should not change your workflow and it isn’t a very big deal when adjusting to the new habit. If not, it could serve as an organizing booster for employees, and most importantly: it keeps your client, stakeholder and internal information safe. On the other hand, ensuring physical security for each of our informational assets is a huge deal. Don’t forget: one of the most prominent threats to keeping what’s confidential safe or accidentally granting unauthorized access, are in fact – the people. You can upgrade your infrastructure to the most state of the art security measures, you can encrypt every bit of data, you can even have 2000 copies of a file for redundancy – all it takes is the wrong person, opening the wrong door for someone or printing something they weren’t aware is classified – and you’re done. A Clean Desk and Clear Screen Policy is like your standard lunch – it might not be as enjoyable – but it’s healthy and keeps you full. You might as well get used to it – who knows, you might enjoy it.
Share this article on:
Sign up for our
newsletter.
Be up-to-date with our latest news, in-depth insights, and privileged content.

Programming Languages
Let’s take a deep dive in time and look at how computer science & programming languages began. Follow us as we go through the ages and look at the timeline, major personalities, and events that through their ingenuity paved the road to our current Technological and Digital Era.
03 Apr 2021

IT Consulting
Software Development
Agile Project Management
The digital age is an exciting time for businesses, as new opportunities abound and technology advances quickly. However, it also poses the age-old question: how do we stay ahead of the competition while navigating this ever-evolving digital landscape? At EBS Integrator, we’ve found the answer to this conundrum lies in optimizing work processes and delivering top-notch IT solutions and products. In this article, we’ll reflect on the importance of these processes and explore how partnering with EBS Integrator can benefit your business.
11 May 2023